Train your incident response team
This is the second part in a post describing how to train your team for incident response and incident investigations.
The first part covered how to analyze the e-mail headers and information in a suspicious e-mail.
Attachment
The e-mail contained one attachment : koen.vanimpe@c.d.zip. Unzipping the file resulted in a .scr file.
-rw-rw-r-- 1 koenvanimpe staff 49152 Feb 4 16:45 franz_krukenberg_str_10_25436_uetersen.scr -rw-rw-r-- 1 koenvanimpe staff 32761 Feb 4 16:45 franz_krukenberg_str_10_25436_uetersen.zip
The sha1 is
99920e112a522e2d1b409e00330022f705c2fec7 franz_krukenberg_str_10_25436_uetersen.scr 630c00846a0242e524d1c17507bf4db47c33b8bb franz_krukenberg_str_10_25436_uetersen.zip
MD5 is
e4b72ce8ea569b12eabf0aef6ed81615 franz_krukenberg_str_10_25436_uetersen.scr a0adb2ccf18f65a102c1c975e7e4baec franz_krukenberg_str_10_25436_uetersen.zip
I uploaded the scr file to Virustotal for further analysis. So far (22-Feb) no-one else submitted a similar sample.
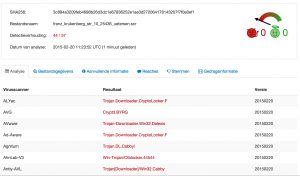
According to Virustotal the file gets recognized by most anti-virus vendors as a CryptoLocker virus.
Symantec describes CryptoLocker.F as :
Trojan.Cryptolocker.F is a Trojan horse that encrypts files on the compromised computer and then prompts the user to purchase a key in order to decrypt them.
CryptoLocker is known as ransomware. The timing in the post by F-Secure describing a rise in CTB-Locker infections corresponds with the time the e-mail was received.
With the use of the Linux command strings I could see that it uses a number of DLLs
cmpbk32.dll KERNEL32.dll SHLWAPI.dll msimg32.dll user32.dll certcli.dll WTSAPI32.dll
The certcli.dll file is a Microsoft DLL that provides communications between a client or intermediary application and certificate services.
The WTSAPI32.dll file is a Microsoft DLL that contains the application programming interface (API) functions that enable application programs to (1) manage terminal services, (2) set and retrieve user configuration information that is specific to terminal services, (3) use terminal services virtual channels, and more, in a terminal services environment.
The SHLWAPI.dll is a Microsoft DLL that is a library which contains functions for UNC and URL paths, registry entries, and color settings.
The file cmpbk32.dll is a Microsoft DLL file which is responsible for a component to Microsoft Connection Manager Phonebook.
With this information we now know that this application has capabilities for
- working with a certificate service
- managing remote services
- working with UNC and URL paths
- working with registry settings
- connecting with the Microsoft Connection Manager Phonebook
These capabilities are confirmed in the remainder of the strings output with calls to
PhoneBookEnumCountries PhoneBookCopyFilter CreateNamedPipe GetCurrentDirectory GetComputerName CreateDirectory UrlCanonicalize CAEnumNextCA CADeleteCA WTSLogoffSession WTSSendMessage
Strings also revealed the use of a library ddi32.dll. As far as I could verify this is a library that helps with drawing. It’s most probably used to build up the notice for the end user that they have a “problem”.
Information before executing the file
When I copied the files to a Windows machine I immediately noticed that the icon of the file mimics to be a Word document. This is done to lure the user into opening the file.
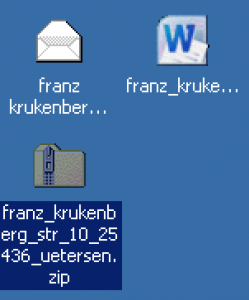
Windows Sandbox – XP
I then decided to execute the file in a virtual machine, a Microsoft Windows XP-SP2. The first step would be to execute it in a VM without external network connectivity. I captured all the network traffic with /Applications/VMware Fusion.app/Contents/Library/vmnet-sniffer in a pcap file.
./vmnet-sniffer -w xp.pcap vmnet1
Opening the file reveals indeed a Word document with the title MARITIME ARCHIVES & LIBRARY Information Sheet 15 ELDER DEMPSTER & COMPANY.
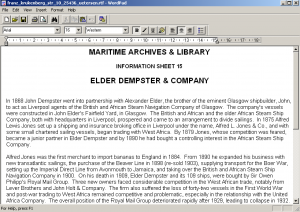
This is a document from the National Museums of Liverpool in the United Kingdom.
After opening the Word document nothing seems to happen. I did not see any network activity at first. After closing the document there was a process that kept running in the background.
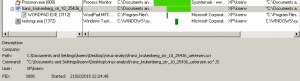
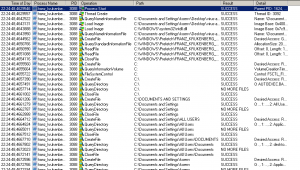
It took a couple of minutes before I could see any “unusual” network requests.
Although Dshell from the US Army provides an easy interface for tracking network activity in a pcap file I decided to use tshark to brush up my knowledge on tshark expressions.
Network capture
There are only two obvious ways network connections from basic malware can happen. Either it connects directly to a hardcoded list of IPs or it does a DNS lookup for a list of hardcoded domains. When I looked at the pcap data I could not see any connections to “unsual” IPs. So I ran tshark against the pcap file to extract the DNS requests and sort them.
tshark -r ../xp.pcap -Y "dns.flags.response == 0" -T fields -e dns.qry.name | sort | uniq -c
Note that on some Linux flavors you have to use -R instead of -Y.
This resulted in a number of domains mostly involving normal Windows operations. Some of the domains however had nothing to do with the network behavior of a normal Windows computer. In this case the domains bikeceuta.com, cargol.cat, ppc.cba.pl and smartoptionsinc.com are queried several times.
25 bikeceuta.com 29 cargol.cat 30 ppc.cba.pl 9 smartoptionsinc.com
According to Symantec, the CryptoLocker virus downloads its message from a number of command and control servers. I assumed that the domains bikeceuta.com, cargol.cat, ppc.cba.pl and smartoptionsinc.com were used by this version of CryptoLocker to download its additional information.
The domains are listed in a number of malware analysis by Sophos : Troj/Agent-ALLW and Troj/Agent-ALMD. The detection date is in line with the date the infected e-mail was received.
The domain bikeceuta.com is registered to somone in Spain. At the time of writing, it resolved to 91.142.215.77. This is an IP in Spain. The website of bikeceuta.com returns a page (in Spanish) of a sports bicycle vendor.

Domain Name: BIKECEUTA.COM Updated Date: 2011-05-03T12:58:28.00Z Creation Date: 2011-05-03T20:58:00.00Z Registrant Name: ERNESTO VALERO MORONTA ... bikeceuta.com has address 91.142.215.77 ... inetnum: 91.142.208.0 - 91.142.215.255 netname: ES-AXARNET-NET descr: AXARNET, Nodo en Madrid country: ES
The domain cargol.cat is registered to somone in Spain. At the time of writing, it resolved to 217.149.7.213. This is an IP in Spain. It’s no longer possible to access the website at cargol.cat. You now get a 403 “You don’t have permission to access / on this server.” message.
Domain Name: cargol.cat Created On: 2006-06-23 17:26:54 GMT Last Updated On: 2014-06-23 09:28:04 GMT Registrant Name: Marc ... cargol.cat has address 217.149.7.213 ... inetnum: 217.149.4.0 - 217.149.7.255 netname: FILNET-2 descr: Filnet static IP addresses for Internet servers country: ES
The domain ppc.cba.pl is registered via a registrar in Belize. At the time of writing, it resolved to 95.211.144.65. This is an IP in Holland (belonging to Leaseweb). The webserver of ppc.cba.pl now returns a page with “Page is blocked”. This is a good indication the hoster is aware of the problem.
created: 2005.01.14 14:36:58 last modified: 2015.02.16 11:45:46 renewal date: 2016.03.15 14:36:58 ... REGISTRAR: Abc Hosting Ltd. #7B Neal Pen Road, Belize City Belize email:domeny@cba.pl ... ppc.cba.pl has address 95.211.144.65 ... inetnum: 95.211.142.144 - 95.211.144.255 netname: LEASEWEB descr: LeaseWeb
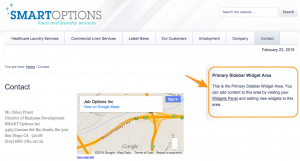
The domain smartoptionsinc.com is registered to somone in the US. At the time of writing, it resolved to 216.70.228.110. This is an IP in the US belonging to Job Options in California. According to the website www.smartoptionsinc.com it is a site of a subsidiary of Job Options Inc, a provider of commercial linen and laundry service for the hospital and healthcare industry. Because of the presence of the “widget area” and blocks I guess that the website is either not finished or abanded. The website is powered by WordPress and reading the HTML source with “/wp-includes/js/jquery/jquery.js?ver=1.6.1” indicate this might be an outdated version of WordPress. Vulnerable WordPress sites are often used in malware campaigns as command and control servers (see for example the CryptoPHP incident)
Registrant: Status: clientUpdateProhibited http://www.icann.org/epp#clientUpdateProhibited Updated Date: 23-dec-2014 Creation Date: 30-dec-2010 Expiration Date: 30-dec-2015 Agundis, Juan Carlos jagundis@joboptionsinc.org Job Options Inc. 3465 Camino Del Rio South Suite 300 San Diego, CA 92108 US ... smartoptionsinc.com has address 216.70.228.110 ... CIDR 216.70.228.96/28 Name JOB-OPTIONS
Out of these four domains, the Polish domain (ppc.cba.pl) has whois data that has been recently updated.
Similar to the information in the e-mail headers there are sources in different countries.
| bikeceuta.com | Spain | ||
| 91.142.215.77 (bikeceuta.com) | Spain | ||
| cargol.cat | Spain (Catalunya) | ||
| 217.149.7.213 (cargol.cat) | Spain | ||
| ppc.cba.pl | Poland | ||
| 95.211.144.65 (ppc.cba.pl) | Holland | ||
| smartoptionsinc.com | United States | ||
| 216.70.228.110 (smartoptionsinc.com) | United States | ||
Conclusions
My experiment so far described how this version of CryptoLocker works. I prevented it from actually starting what it is supposed to do by blocking the network access. The next steps involve having it run in a fully networked environment and observe what happens.
Blocking the network access to the command and control servers does not prevent CryptoLocker from starting but it prevents it from doing direct harm to your documents. This is a good reason for having a network setup that blocks outgoing connections to blacklisted domains. Everything depends of course on the quality of the blacklist. It certainly is not a perfect solution but an extra layer of defense.
Also note that some malware checks if it’s being run in a virtualization environment. This was not the case for this sample which made it easier for me to do the analysis.
If you only consider the geographical location and language then the source of this malware could be something Spanish or Central America based. This is highly speculative and it could also be rather a coincidence. Two command and control servers are located in Spain and registered with a Spanish or Catalonian TLD. The registration of one command and control server is in Belize (Central America). The sender IP is in Mexico. One of the IPs of a command and control server is in California (near Mexico).
IOCs
Based on the information from part 1 and this part we can deliver simple to use IOCs :
- Filter attachments with a name similar to full.username@organisation.tld.zip
- Reject SMTP connections from 132.248.193.220
- Block network traffic to bikeceuta.com
- Block network traffic to cargol.cat
- Block network traffic to ppc.cba.pl
- Block network traffic to smartoptionsinc.com
Run in a networked VM
The last part of this post describes the behavior of this virus an a networked VM.


Thanks for this interesting blog! Wonder if you could send me the pcap you captured using vmnet-sniffer. Appreciate it.
Hi Jin. Thank you for the feedback. Unfortunately I no longer have the pcap file in my possession.
Quality articles or reviews is the main to attract the users to visit the web
site, that’s what this website is providing.
Spot on with this write-up, I really feel this website needs far
more attention. I’ll probably be back again to read through more,
thanks for the information!