Basic forensic investigation
For a recent project I had to do a basic forensic investigation of a hard drive. The assignment included two questions :
- detect if there were viruses on the system
- analyzing the surf behavior of one of the users (policy related)
I want to share the steps that I took to do basic forensics on a cloned disk image. This is not an in-depth forensic investigation but it was enough for this assignment.
The investigation included three machines
- The laptop (hard drive) to investigate
- A secure Ubuntu Linux laptop to clone the disk to a disk image, export the image via attached storage and hold a virtual machine
- A Windows 7 virtual machine (running on the Linux laptop) for the bulk of the investigation. This VM was prepared on an OSX laptop and then finalized on the Linux laptop.
Note that taking into consideration that the original evidence was already contaminated by a prior research, the steps taken were enough for providing “clean evidence”.
Hardware
The device to investigate was a Windows 7 installation on a Lenevo laptop with a Seagate 320GB hard drive.
I disconnected the hard drive and removed it from the laptop.
I used two (one master and one working copy) external storage devices for storing all the investigation details.
Disk image
I connected the hard drive to a laptop running a fresh install of Ubuntu Linux 14.04.2 LTS. I disabled the auto-mount options. This has been described on the Ubuntu wiki. Disabling auto-mounting is necessary to make sure that nothing changes on the original disk. Ideally you use a write-blocker to accomplish this but for this investigation using the read-only option with no mounting on Linux was enough.
The external hard drive showed up as device /dev/sdc. I wanted to create a full disk image, including all the available partitions.
Disk layout
As a first step, for documentation purposes, I listed the disk layout with fdisk.
fdisk /dev/sdc
Print out the layout with the p option.
Disk /dev/sdc: 38913 cylinders, 255 heads, 63 sectors/track Units = cylinders of 8225280 bytes, blocks of 1024 bytes, counting from 0 Device Boot Start End #cyls #blocks Id System /dev/sdc1 * 0+ 38- 39- 307200 7 HPFS/NTFS/exFAT end: (c,h,s) expected (38,94,56) found (40,184,56) /dev/sdc2 38+ 36969- 36931- 296647680 7 HPFS/NTFS/exFAT start: (c,h,s) expected (38,94,57) found (40,184,57) end: (c,h,s) expected (1023,254,63) found (1023,239,63) /dev/sdc3 0 - 0 0 0 Empty /dev/sdc4 0 - 0 0 0 Empty
This shows that the Windows hard drive has two partitions, the boot (/dev/sdc1) and the system (/dev/sdc2) partition.
Clone a disk
The easiest way to create full disk images with Linux is with dd.
sudo dd if=/dev/sdc of=/storage/sdc.dd bs=65536 conv=noerror,sync
The options of dd are
- noerror : continue after read errors
- sync : use synchronized I/O for data and metadata
- bs=65536 : write 65536 at a time
This resulted in a full disk image, containing both partitions : boot and system (including the data).
Hash the disk image
In order to guarantee the integrity of the image I made a hash of the image, both with MD5 and SHA1.
md5sum /storage/sdc.dd sha1sum /storage/sdc.dd
Creating a hash of the image file allows you to check in the future that nothing has changed in the original image, preserving the original evidence.
All of this gave me a full forensic clone of the drive image, available under /storage/sdc.dd.
Accessing the image
Now that the full disk image was ready I had to examine it. The majority of the tools available for examining a disk image run on Windows. So I installed a fresh Windows 7 virtual machine and had the dd disk image available via a file share (z:).
One of the easiest tools available to read disk images is FTK Imager. You can use the freely available download of FTK Imager from the website of Access Data.
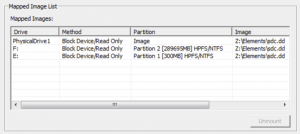
With FTK Imager you point it to a disk image and then mount the available drives. In this case it resulted in (Windows) having drive E: and F: available (in read-only modus) for further research. For the remainder of this post :
- F: is the system drive, retrieved from the disk image
- E: is the boot partition, retrieved from the disk image
Via FTK Imager you can investigate the files available on the disk but also those that have been deleted (via ‘Unallocated Clusters’) or backed up (in the ‘Volume Shadow Copies’).
Listing users
This investigation focused on a domain user. If you happen to have to do an investigation on a local user it makes sense to document the different user details that you can find in the registry hives.
The user related information can be found in the SAM registry database at [root]\Windows\System32\config\SAM. I use FTK Imager to export the SAM database. Next to the SAM database you’ll also find the SECURITY, SYSTEM, SOFTWARE and DEFAULT database. Do not focus your investigation only on the current registry database. Windows creates backups of the registry in the RegBack directory and these files can also contain useful information.
You can then use FTK Registry Viewer to list the user details.
Finding viruses
The first question of the request was to detect if there were any viruses on the system. I used the free version of Avira to scan both the E: and F: device.
The scan via Avira returned a number of possible viruses. I then used Panda Free Antivirus to double check these results. Both scan results had more or less the same hits.
I then used FTK Imager to export the files marked as containing a virus. When you export the files with FTK Imager you can also include the hashes. This results in a CSV file (note, both hashes and filenames are anonimized)
MD5,SHA1,FileNames "25d6a149ff6010698XXX","XX13d35fe40aaa5a3","\\.\PHYSICALDRIVE1\Partition 2 [289695MB]\System [NTFS]\[root]\Users\xxx\AppData\Local\Temp\xxx.tmp"
Once the files were exported I used the hashes of the files and searched VirusTotal to check the behavior of these files. All files detected by the virusscanners were already previously analyised by VirusTotal. The findings of the two virusscans together with the results from VirusTotal provide a good insight on the nature and impact of the found viruses.
The details from these three sources provided me enough data to answer the first question and backup the answer with proof from the AV- and VT-reports.
Analyze surf behavior
The second question was to check if the surf behavior of a user corresponded with a given policy.
The surf history is available in a number of places (in both deleted and non-deleted files) and depends on the browser being used. Instead of carving all the different files manually I decided to use a tool to do this. I used a trial version of Internet Evidence Finder from Magnetic Forensics. IEF is available as a one month trial version. The trial is great to explore the different features but if you’re going to use it for business purposes you should request a quote.

Within IEF, I enabled all the web-related and operating-system related plugins. This allows you to search for the necessary evidence concerning the ‘web-browsing’. Note that IEF has also plugins for other searches (Skype, Facebook, listing users, P2P, will also reveal other (Skype, Facebook, …).
The first step in IEF requires you to point it to a source. I choose to have it analyze the dd disk image. Because IEF was running in a VM and the disk image was mounted on external storage the analyze process took quite a while.
Once the process is done you have to open the report viewer to see the results. Because IEF reads all the files that were made available via FTK Imager it analyzes both the files normally available on the disk and the deleted files (available via the ‘Unallocated Space’).
For example in the screenshot below you see a record of a visit to Facebook that has been found in the unallocated clusters (meaning the ‘deleted files’).
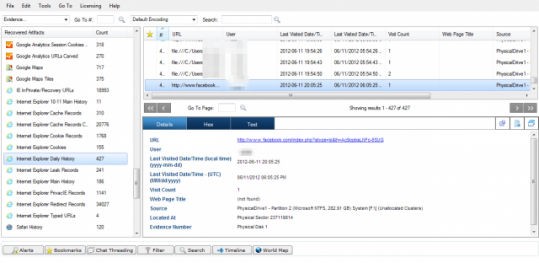
IEF returns a database of information found in the different files and a timeline of what happened. The timeline shows you the different actions of the user over time. This is based on different resources like for example the Windows Event Log, the cookies found, the Google Analytics cookies and all other relevant files. Not that this also includes deleted files and files in the Volume Shadow Copies.
Via IEF I was able to extract the websites that were visited (based on cookies, IE history and Google Analitycs cookies). It allowed me to get a list of web visits per certain category. Combining this information with the timeline gave me the opportunity to reconstruct the web surfing behavior and provide an answer to the second question of the request. I was able to backup the answer with proof by exporting the files that contained the proof (cookies, etc.) via FTK Imager and by exporting the results (in CSV format) from IEF.
Reconstructing events with IEF
Combining the timeline feature with other events allows you to reconstruct in detail what happened prior or after a given timestamp. This is great if you to find out for example what possible visit to a website caused a virus infection.
In an earlier stage I detected the presence of a virus infected file. According to the information from VirusTotal this virus exploited a vulnerability in Java (CVE-2012-1723). With FTK Imager it was possible to detect the “last modified date” (for this case it was in the DOS format field). I then used IEF to zoom in on the actions that happened just before that timestamp. According to the data found in Google Analytics Referral I found out that the user did a search via Yahoo. The same timestamp then showed, via Google Analytics Session and Google Analytics First Visit a visit to a website from the search results. This was confirmed with the timestamp when the cookie was set in the Internet Explorer Cookie database. A couple of seconds after the creation of the cookie the timeline revealed entries in the Windows Event Log. These entries describe how java.exe was started.
<ExePath>C:\Program Files (x86)\Java\jre6\bin\java.exe</ExePath>
I reconstructed the event time line as follows :
- Get last modified date from virus via FTK Imager
- Use Internet Evidence Finder to zoom in on the timeline a couple of seconds before the last modified date timestamp
- Use Google Analytics Referral to extract the user web action (a Yahoo search)
- Use Google Analytics Session and Google Analytics First Visit to confirm visit to one of the search results
- Confirm the visit with data present in the Internet Explorer Cookie database
- Add the different Windows Event Log entries
These series of events make it very likely that the virus was installed by visiting one of the sites from the search results.
Note that some of these entries (espc. the Google Analytics cookies) were found in the Volume Shadow Copies. This shows you that you have to look in every information resources available.
If you want to learn more about extracting information from Google Analytics cookies then you should definitely read the blog posting Carving for Cookies: Supersize your Internet History Timeline using Google Analytic Artifacts.
Summary
This project gave me a short insight in doing a basic forensic research and provide an answer on two simple questions. In short I followed these steps
- Make the image with dd
- Mount the image to Windows drives with FTK Imager
- Scan the system with a virus scanner
- Export files that need to be analyzed with FTK Imager
- Use VirusTotal to check the behaviour of potential viruses
- Combine antivirus and VirusTotal reports
- Analyze the web behavior with Internet Evidence Finder
- Use data from unallocated space, shadow copies and non obvious cookies
- Use a timeline to zoom in on infection dates
- Extract all the files of interest, include the timestamps, file hashes, the location where they were found and how you extracted them


It’s berger to mount the hdd in read only
great, it helps me in my report 🙂
thanks
Just a query i had, if i want to prove in a court that the image taken from a HDD does actually belong to it and has not been taken from anywhere else, how can that be done.
And BTW its a good article describing about the basic process of disk analysis.
Thanks!
Some forensic tools (FTK if I remember correctly) list the disk serial number. Make a copy (photo) of the disk showing it’s serial number.
Thanks for your reply. I also thought of the same thing but just wanted to understand whether it is a standard procedure a not.
Very good! Thank you,
Hi,thanks for this good article