Unified Audit Log
The Unified Audit Log contains crucial elements when you want to investigate an incident in O365. You can do this live (with PowerShell, for example via Hawk). Sometimes however you receive the log file offline, with no live access to the environment.
I could not find a tool that gives me a quick overview of what was in the log. So I decided to write my own simple Python script to parse the exported O365 Unified Audit Log.
The exported Unified Audit Log is in CSV and basically you only need the first field of that CSV file, AuditData. This field is a JSON set of data with all the useful data.
Test data
There is a public data set containing Office 365 Unified Audit Logs for security research and detection. I used this data set to demonstrate/tune the script. The screenshots in this post are made with running the script on that data set.
Script
I was interested in the type of operations taking place, from where they are initiated and which objects they manipulated. And this is exactly what the script outputs. There’s plenty of room for improvement but for now it returns the results I’m interested in.
- Overview of basic elements of the log file
- Type of operations
- Client IPs
You can find the script on Github https://github.com/cudeso/tools/blob/master/O365-python-parse/o365-python-parse.py.
Overview of the log
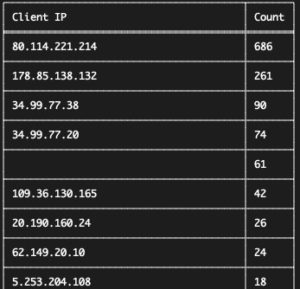
Client IPs
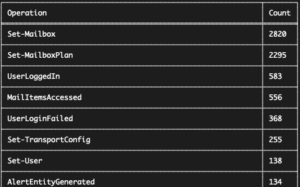
Type of operations taking place
Update 20230214
Added support for simple output to CSV via https://github.com/cudeso/tools/commit/7e3132c6e727cbfdb732a26532785e7bb3af232e.

